The Real Cloud Security Gap isn’t Tools or Talent, it’s Structure
For years, cloud security failures were explained as a maturity problem. Organisations were told they were early, moving fast, and would eventually stabilise as tools improved and teams caught up. The 2026 Cloud Security Report suggests that the explanation no longer holds.
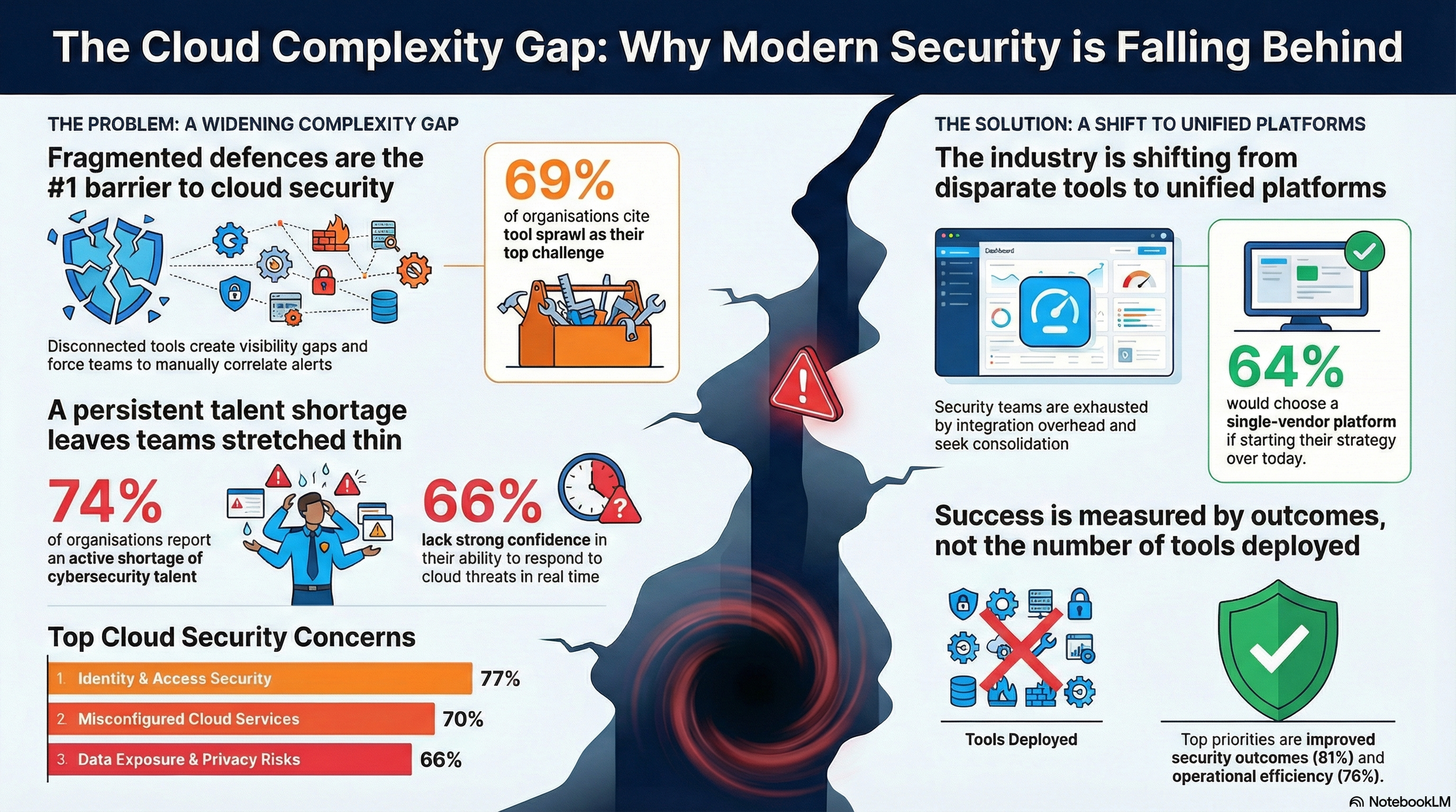
Based on a survey of 1,163 senior cybersecurity leaders worldwide, the report identifies a widening “cloud complexity gap,” defined not as a funding shortfall but as a structural mismatch between how cloud environments now operate and how security is still organised. Budgets are rising, cloud security now accounts for more than a third of IT security spend, and yet most organisations remain stuck in early maturity stages.
The implication is uncomfortable but clear. Cloud security is not lagging because organisations are behind. It is lagging because the model itself is misaligned with reality.
Complexity is no longer accidental
One of the report’s most important findings is that cloud complexity is no longer transitional. It is permanent.
According to the data, 88% of organisations now operate hybrid or multi-cloud environments, with 81% relying on two or more cloud providers for critical workloads and nearly a third using more than three. These environments evolve incrementally, driven by business expansion, regional requirements, and modernisation initiatives rather than central design.
The report is explicit about the consequences. Every additional provider, service, or identity introduces new configurations, permissions, and data paths. Infrastructure scales automatically, but understanding does not. As the report notes, “the entire ecosystem becomes increasingly complex to understand,” even as security teams are expected to secure it by design.
This matters particularly in the Middle East, where cloud strategies are shaped by a mix of hyperscaler adoption, sovereign cloud initiatives, and sector-specific regulation. Financial services, energy, aviation, and government platforms frequently span global cloud providers alongside local infrastructure mandated by data residency rules. The result is not simplification but layered complexity.
Fragmentation has become the primary risk driver
The report identifies fragmentation, not attackers, as the most immediate operational threat.
Nearly 69% of organisations cite tool sprawl and visibility gaps as the top factor limiting cloud security effectiveness. As environments fragment across clouds, identity systems, and SaaS platforms, security controls fragment alongside them. Telemetry is siloed. Policies drift. Alerts multiply without shared context.
This fragmentation directly undermines confidence. Sixty-six percent of organisations lack strong confidence in their ability to detect and respond to cloud threats in real time, a figure that has increased year over year despite higher investment.
Vincent Hwang summarises this dynamic in the Word document, noting that security solutions are “frequently without coordination, resulting in disconnected tools and limited end-to-end visibility”. The report’s data shows that this is no longer an edge case. It is the dominant operating condition.
In Middle Eastern enterprises, fragmentation is often masked by compliance success. Controls may meet regulatory checklists while still failing to provide a unified view of exposure across clouds, identities, and data flows.
Spending more has not produced maturity
One of the report’s most striking findings is the disconnect between investment and outcomes.
Cloud security budgets are rising, with 62% of organisations expecting further increases, and cloud security now representing 34% of total IT security spend. Yet 59% of organisations still classify their cloud security posture as “initial” or “developing.”
The report does not interpret this as overinvestment. Instead, it highlights diminishing returns caused by architectural fragmentation. Each new tool adds integration overhead, additional consoles, and operational decision fatigue. Much of the spend is absorbed by managing complexity rather than reducing exposure.
Hwang reinforces this point, writing that the growing gap between complexity and resilience “is not due to a lack of investment,” but to the fact that defences are not keeping pace with modern cloud use cases, many of which now include AI elements.
For Gulf economies investing aggressively in AI-driven services and digital government platforms, this finding is particularly relevant. It suggests that simply allocating more budget to cloud security will not automatically translate into stronger control.
Talent shortages turn complexity into risk
The report makes clear that human capacity is now a limiting factor.
Seventy-four percent of organisations report an active shortage of cybersecurity talent, with cloud-specific skills among the hardest to source . These shortages amplify fragmentation. Disconnected tools generate alert volumes that exceed the capacity of already stretched teams, forcing a reactive, alert-driven posture.
The report notes that proactive threat hunting, architectural improvement, and automation refinement are increasingly deprioritised due to lack of capacity. Manual processes simply cannot scale to environments that change continuously.
In the Middle East, where cloud adoption has outpaced the development of local cybersecurity talent pools, this dynamic is especially pronounced. Many organisations rely on small internal teams overseeing complex, multi-cloud estates that underpin nationally critical services.
Attackers exploit the gaps between domains
The report also clarifies where risk concentrates.
Identity and access security ranks as the top concern for 77% of organisations, followed by misconfigured services and data exposure . These risks are not independent. The report describes an “exposure chain” in which misconfiguration, excessive permissions, and sensitive data combine to create direct attack paths that point solutions fail to detect in isolation .
Attackers understand this structure. They use automation to map identity paths, discover misconfigurations, and identify exposed data faster than siloed defences can correlate signals. As the report notes, the challenge is no longer detection alone, but containment at sufficient speed.
Why consolidation is being reconsidered
Against this backdrop, organisations are rethinking how cloud security should be architected.
When asked how they would design their security strategy if starting fresh, 64% said they would choose a single-vendor platform unifying network, cloud, and application security. The report stresses that this preference reflects operational reality rather than vendor ideology. Security teams are exhausted by integration overhead and are seeking shared telemetry, policy, and context across domains.
The emphasis is not on fewer tools, but on unified visibility and coordinated enforcement, which the report identifies as prerequisites for effective automation and AI-driven defence.
What this means for the Middle East
For Middle Eastern organisations, the report’s conclusions point to a strategic inflection point.
Cloud security challenges in the region are not primarily about adoption speed or budget allocation. They are about operating models that were designed for simpler environments and are now being stretched across complex, regulated, multi-cloud estates.
The 2026 Cloud Security Report shows that progress comes not from adding controls, but from reshaping how security operates day to day. Unified visibility, reduced fragmentation, connected risk domains, and automation grounded in shared context are no longer optional. They are structural requirements.
As the report concludes, organisations making progress are those that define success by outcomes rather than tools, measuring effectiveness through reduced exposure, faster response, and sustained operational confidence .
For a region building its economic future on digital infrastructure, that shift is not theoretical. It is foundational.